Difference Between WPA2 and WPA3
WPA, short for Wi-Fi Protected Access is a security standard designed for wireless networks to make them secure and protected from unauthorized access. The Wi-Fi Alliance released WPA in 2003 because IEEE’s security update was taking too long and the WEP was considered insecure at that time. The Wi-Fi Alliance simply named the first generation as WPA instead of WPA1 which was specifically designed for better user authentication and data encryption than its WEP counterpart. WPA was based on parts of 802.11i and included 802.1x authentication, and TKIP. The WPA was superseded by its more efficient successor WPA2 in 2004. In 2018, the Wi-Fi Alliance released the next version called WPA3 as a future replacement for WPA2, adding significant updates in regards with security for wireless networks. Let’s summarize some basic differences between the two standards – WPA2 and WPA3.

What is WPA2?
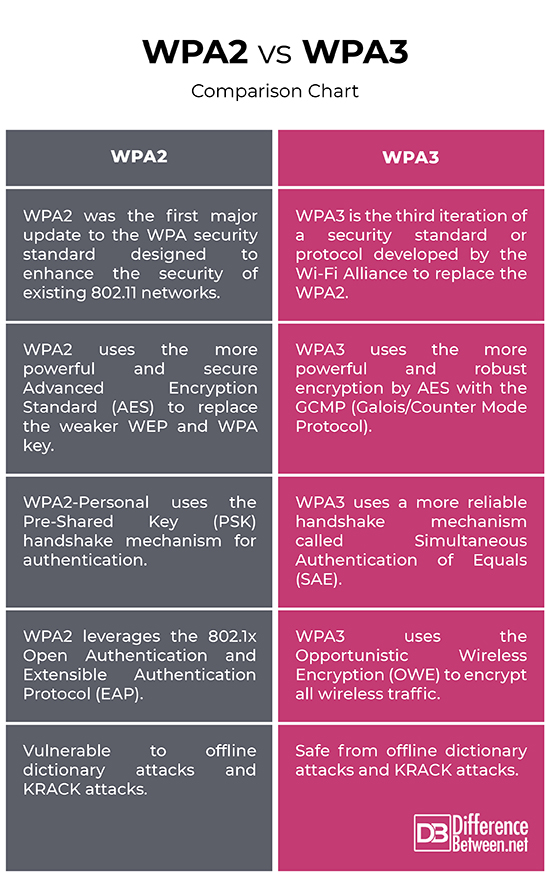
WPA2, short for Wi-Fi Protected Access II, is the first major update to the WPA security standard designed to enhance the security of existing 802.11 networks. The idea was to design something that could be deployed with a simple firmware upgrade without worrying about upgrading the hardware. WPA2 replaces the weaker WEP key with the superior and more robust AES CCMP algorithms, designed to replace the TKIP. It is much powerful and more reliable than the original TKIP protocol. The WPA2 standard was based on the completed 802.11i specifications, which mandate the use of 802.11x authentication. It is commonly used to protect wireless networks using two encryption methods – AES (Advanced Encryption Standard) and TKIP (Temporary Key Integrity Protocol). But, it still has its vulnerabilities, one of which is that AES is very computationally intensive. Besides, it is still a robust encryption standard which is very hard to hack into.

What is WPA3?
WPA3, short for Wi-Fi Protected Access 3, is the third iteration of a security standard or protocol developed by the Wi-Fi Alliance and announced in 2018. WPA3 was designed to replace the WPA2 security standard, adding several security enhancements and tackling security vulnerabilities of the WPA2 to better secure personal and enterprise wireless networks. WPA3 uses a more powerful and robust encryption by AES with the GCMP (Galois/Counter Mode Protocol). Unlike WPA2, it uses 192-bit encryption meaning 192 probable combinations of zeroes and ones for every bit that is encrypted. It is the next generation of security protocol that takes wireless security to the next level, enabling more robust authentication and delivering improved cryptographic potency for mission critical enterprise networks. It includes other features such as Simultaneous Authentication of Equals (SAE), Protected Management Frames (PMF), and Forward Secrecy.
Difference between WPA2 and WPA3
Basics
– The Wi-Fi Protected Access II (WPA2) was the first major update to the WPA security standard designed to enhance the security of existing 802.11 networks. WPA2 superseded WPA security standard in 2004, replacing the weaker WEP key with an enterprise grade encryption standard favored by corporations. In 2018, the Wi-Fi Alliance announced the next iteration called WPA3 to replace the WPA2, adding several security enhancements and features while overcoming the security vulnerabilities of the WPA2. It takes security to the next level by making wireless networks future ready.
Encryption
– WPA2 uses the Advanced Encryption Standard (AES) to replace the weaker WEP and WPA key. AES is a powerful encryption standard used for all wireless networks that contain sensitive data and leverages 802.1x or Pre-shared keys to protect home networks, rather than the deprecated TKIP standard. WPA3, on the other hand, uses the more powerful and robust encryption by AES with the GCMP (Galois/Counter Mode Protocol) and replaces the PSK with the more reliable and secure handshake mechanism called Simultaneous Authentication of Equals (SAE).
Wireless Protocol
– WPA2 uses a strong encryption technology called Wi-Fi Protected Setup (WPS) – a wireless security standard that makes connection between a router and wireless devices much faster and easier. WPA3, on the other hand, uses the much powerful and enhanced system called Wi-Fi Device Provisioning Protocol (DPP), allowing users to utilize NFC tags or QR codes to allow wireless devices on the networks, without worrying about passwords. DPP replaces the readily exploitable WPS.
Authentication
– WPA2 leverages the 802.1x Open Authentication and Extensible Authentication Protocol (EAP), which is an extension to the PPP protocol suite. EAP does not perform authentication or encryption on its own; in fact, it works with other authentication or encryption standards to authenticate the credentials of clients and servers. WPA3 improved upon the WPA2’s open authentication support by using something called the Opportunistic Wireless Encryption (OWE) to encrypt all wireless traffic.
WPA2 vs. WPA3: Comparison Chart
Summary
In a nutshell, wireless networks of all kinds gain an upper hand when it comes to security because of the WPA3 security standard which improves upon everything WPA2 offers. In addition, WPA3 security protocol streamlines everything and how security protocols are implemented throughout wireless networks. Also, WPA3 beefs up the 802.11’s open authentication support by offering something robust and more reliable called the Opportunistic Wireless Encryption (OWE). The idea behind OWE is to provide encrypted communication without having to use passwords; instead, every device on the network gets its own unique key. Well, WPA2 is still a widely used wireless security standard but it’s not without its vulnerabilities.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Fleishman, Glenn. Take Control of Wi-Fi Networking and Security. California, United States: Alt Concepts Inc., 2019. Print
[1]Odom, Wendell. CCNA 200-301 Official Cert Guide Library. Indiana, United States: Cisco Press, 2019. Print
[2]Chandra, Praphul et al. Wireless Networking: Know It All. Amsterdam, Netherlands: Elsevier, 2007. Print
[3]Weeks, Roger and Rob Flickenger. Wireless Hacks. California, United States: O’Reilly Media, 2005. Print
[4]Lammle, Todd. CCNA Certification Study Guide, Volume 2 Exam 200-301. New Jersey, United States: John Wiley & Sons, 2020. Print
[5]Image credit: https://de.wikipedia.org/wiki/Wi-Fi_Protected_Access#/media/Datei:Fritz!Box_Fon_WLAN_7141_-_Typenschild-3743.jpg
[6]Image credit: https://live.staticflickr.com/690/20944901840_02a0f85c75_b.jpg
