Difference Between APT and Most Malware
Rapid growth in cyber attacks and the design of sophisticated malware tools is not only causing a great matter of concern for the global IT industry but also defense and banking industry as well. Organizations realize that cyber security is a great concern for the whole fraternity and resourced need to be allocated to protect the integrity of an organization. We are at a point when cyber risk is fast becoming an additional cost of doing business on the web. The implications are far reaching as the mobilization of the Internet expands to a variety of devices and spawns new industries. Recently, the term APT, short for Advanced Persistent Threat, has become the common tool for cyber warfare. But what exactly it means? Persistent is a relative term, but if you assume it means that an attacker won’t give up until when met with trivial countermeasures, then of course, the attacker is persistent. It’s a completely different problem and until an organization fully understands it, they will not be able to fix the problem. Most malware are very different from the new age APTs. Let us examine how.
What is Advanced Persistent Threat (APT)?
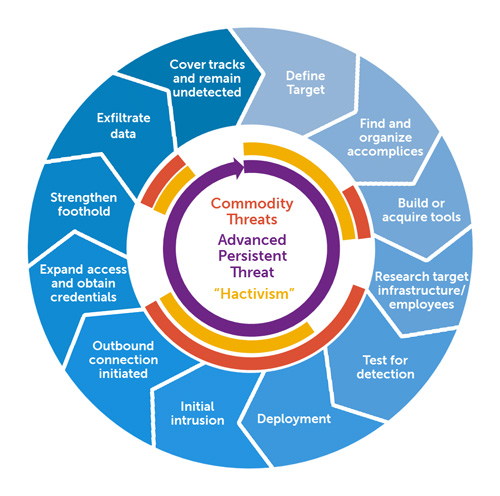
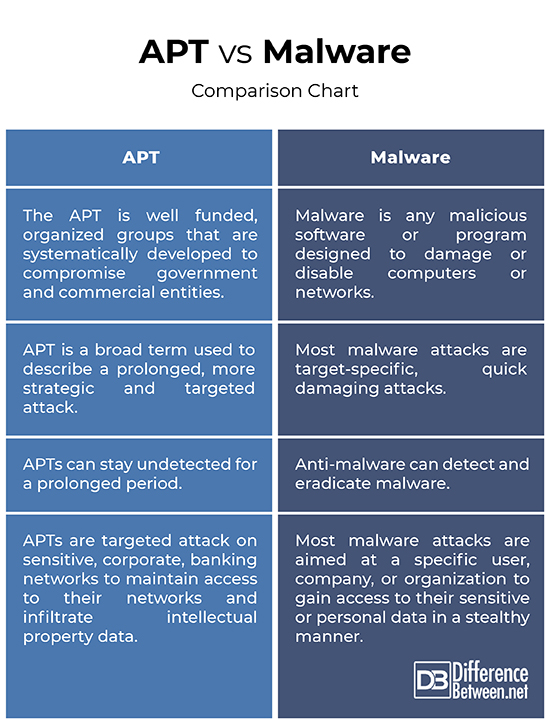
APT, short for Advanced Persistent Threat, is a cyber-adversary and a combination of several sophisticated cyber attacks which composed of advanced logistical and operational capability for long-term intrusion campaigns. It is a prolonged and targeted attack on sensitive, corporate, banking networks to maintain access to their networks and infiltrate intellectual property data as well as information that is economically and politically beneficial. The APT is well funded, organized groups that are systematically compromising government and commercial entities. The term was originally developed as a code name for Chinese-related intrusions against US military organizations. The ATP attacks are stealthy and target-specific which is quite different than traditional worms, viruses or malware. The goal is to remain undetected for an extended period of time to gather sensitive data.
What is Malware?
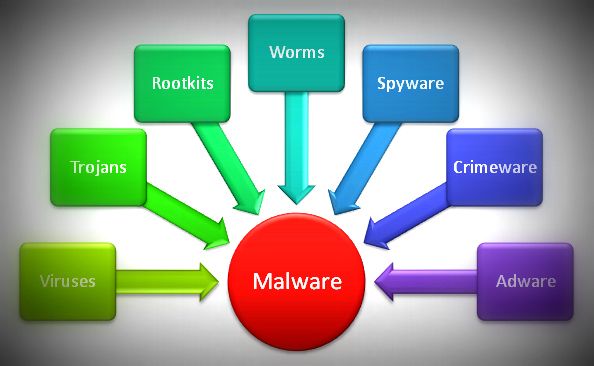
Most malware attacks, unlike APTs, are quick damaging attacks to subvert the integrity of Internet operations. Malware is nothing but a set of instructions that run on your computer like a software application and make your system do something that an attacker wants it to do. Most malware attacks are carried out to steal intellectual property, conduct cyber espionage, and damage critical infrastructure. These are targeted cyber attacks intended to manipulate the system by providing executable instructions inside of user input. They can achieve both tactical and strategic goals across the Internet without requiring any physical encroachment. It is easy to underestimate the impact and capabilities of targeted malware attacks that aim at a specific user, company, or organization.
Difference between APT and Most Malware
Execution
– Advanced Persistent Threat, or APT, is a combination of several sophisticated cyber attacks which composed of advanced logistical and operational capability for long-term intrusion campaigns. APT is a broad term used to describe a prolonged, more strategic and targeted attack which is quite different than traditional worms, viruses or malware. Most malware attacks are target-specific, quick damaging attacks like Trojans and phishing in which an attacker create malicious software that’s installed on the victim’s system without the consent of the user. Different malware have varying capabilities. APTs are an entirely different story.
Target
– APTs are small in number compared to most malware attacks and are considered a serious, costly threat. It is a prolonged and targeted attack on sensitive, corporate, banking networks to maintain access to their networks and infiltrate intellectual property data as well as information that is economically and politically beneficial. The attack is carried out by a professional attacker on specific sensitive organizations. Most malware attacks are a class of dedicated attacks aimed at a specific user, company, or organization to gain access to their sensitive or personal data in a stealthy manner.
Protection
– The best way to deal with most malware attacks is to avoid opening suspicious mails or download unverified attachments in the first place. All the network devices and web applications running on the Intranet must be thoroughly and regularly audited for unknown vulnerabilities. Security assessments help solidify network security and eradicate critical security flaws. Coming to protection against APT attacks, choosing a reliable firewall is the first layer of defense against APTs. APTs are new-age threats that use advanced techniques to avoid detection and can stay undetected for a long time. So, a robust security system is required to detect, analyze and eradicate APTs.
APT vs. Malware: Comparison Chart
Summary of APT vs. Malware
Typically, APT refers to China or some other nation-state or well-funded and established criminal entities who want to compromise a very specific sensitive organization. The term was originally used as a code name for Chinese-related intrusions against US military organizations. But as the technology progresses, the term has evolved into advanced adversaries that are hell-bent on exploiting information and sensitive data in a more covert manner. On the contrary, most malware attacks are plain, quick damaging attacks aimed at a specific individual, company, or organization to manipulate their system or network by providing executable instructions inside of user input, as opposed to APTs which take a more strategic, systematic approach.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Image credit: https://commons.wikimedia.org/wiki/File:Tipos-de-malware.jpg
[1]Image credit: https://commons.wikimedia.org/wiki/File:Advanced_persistent_threat_lifecycle.jpg
[2]Bone, James. Cognitive Hack: The New Battleground in Cybersecurity ... the Human Mind. Boca Raton, Florida: CRC Press, 2017. Print
[3]Cole, Eric. Advanced Persistent Threat: Understanding the Danger and How to Protect Your Organization. Waltham, Massachusetts: Syngress, 2012. Print
[4]Winkler, Ira and Araceli True Gomes. Advanced Persistent Security. Waltham, Massachusetts: Syngress, 2016. Print