Difference Between Spear Phishing and Whaling
Cyber criminals have been frequently carrying highly targeted email fraud attacks to compromise corporations and financial institutions worldwide. These attacks, called phishing attacks, use trickery to access and steal user data such as login credentials, credit card numbers, and other sensitive data. The attacker disguises as a trusted party and deceives the victim into opening an email or a text message. Next, the victim is duped into clicking a link, which installs malicious code on their computer. This kind of attack can be damaging and may lead to identity theft, unauthorized purchases, or stealing of funds.
Phishing attacks can be broadly categorized as ‘spear phishing’ and ‘whaling’. Spear phishing is somewhat similar to whaling attacks because of their similar natures, except whaling attacks are target-specific where the target is someone of significance or importance. A spear phishing attacks rather targets a specific organization or group. Although, spear phishing appears like whaling attacks, it is a little different from typical social engineering attacks.
What is Spear Phishing?
Spear phishing is a subset of phishing but it is targeted at a specific organization or group rather than a random set of people. This is a form of target-specific social engineering attack where the perpetrator masquerades as a trusted individual and tricks the victim into clicking a malicious link in a spoofed email or a text message, which installs malicious code on their computer or network. After that, the attacker is able to retrieve sensitive personal and professional data from the victim and at times allows them access to the affected computer. These email phishing attacks target specific individual and often contain personal information such as employee names and contact numbers, mailing addresses, social security numbers, and credit card numbers. The goal is to gain access to corporate banking information and other sensitive information to facilitate further financial fraud, larceny, and other cyber crime.
What is Whaling?
Whaling is yet another variation of spear phishing attack, except whaling targets high-level executives or decision makers of an organization. The person targeted is someone of significance or importance; it might be a CEO, COO, or CTO of an organization. These attacks typically take specific responsibilities of these executive roles into consideration, using focused messaging to trick them. The attack is based on the assumption that these people have more sensitive information to divulge, such as password to admin accounts, trade secrets, etc. The attacker sends an email pretending to be an organization, such as a client. The message is so specific that it may seem legitimate enough for the victim to act and click a link containing malicious code that is installed on his/her computer, or else it may redirect to a website or webpage under the hacker’s control.
Difference between Spear Phishing and Whaling
Definition
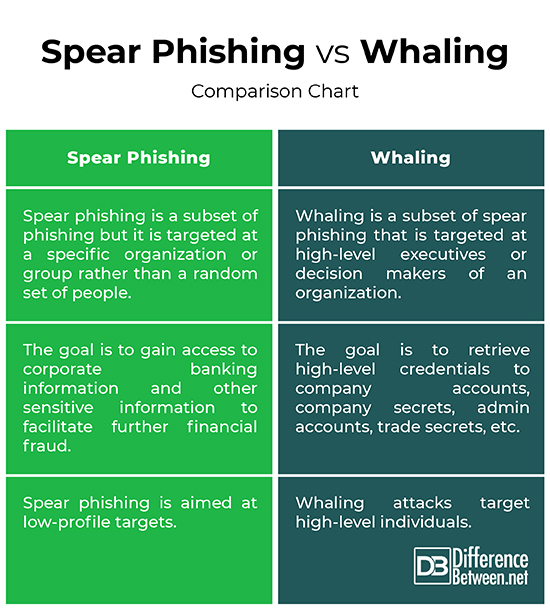
– Spear phishing is specific form of phishing which targets a specific organization or a group of people rather than a random set of people. The perpetrator sends a malicious email pretending to be a trusted party to as many users as possible and tricks the victim into clicking a malicious link in a spoofed email or a text message, which installs malicious code on their computer or network. Similarly, whaling is a subset of spear phishing that is targeted at high-level executives or decision makers of an organization, who has much more critical information to lose than the average user.
Target
– Spear phishing and whaling attacks are very different in terms of their sophistication levels and the victims they target. A spear phishing attack is customized to target an organization or specific individual(s) in order to gain access to corporate banking information and other sensitive information to facilitate further financial fraud. Whaling, on the other hand, targets an organization’s high-level members or C-level executives, such as CEO, COO or CTO, in order to retrieve high-level credentials to company accounts, company secrets, admin accounts, trade secrets, etc. While whaling attacks target high-level individuals, spear phishing is aimed at low-profile targets.
Mitigation
– The most effective measure to safeguard your computer or network from spear phishing attacks is to educate people on social engineering techniques. Spear phishing emails are not easy to detect, so it’s wise to check the destination of on any clickable links before actually clicking on the links. Other measures include two-factor authentication and password management policies. Whaling requires the same sort of protections as other social engineering attacks such as proper malware and antivirus protection, and above all, user awareness. The same techniques used to mitigate spear phishing attacks can also apply to whaling.
Spear Phishing vs. Whaling: Comparison Chart
Summary
In a nutshell, spear phishing and whaling attacks are very different in terms of their sophistication levels and the victims they target. While whaling attacks target high-level individuals, spear phishing is aimed at low-profile targets. The attacker disguises as a trusted party and deceives the victim into opening an email or a text message. Next, the victim is duped into clicking a link, which installs malicious code on their computer. While whaling targets C-level executive or decision makers in high levels of an organization, the same techniques used to mitigate spear phishing attacks also apply to whaling. The best measure to deter the success of whaling attacks is to use digital signatures.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
1 Comment
Leave a Response
References :
[0]Howard, Rick. Cyber Fraud: Tactics, Techniques and Procedures. Boca Raton, Florida: CRC Press, 2009. Print
[1]Samuelle, T.J. Mike Meyers' CompTIA Security+ Certification Passport, Third Edition (Exam SY0-301). New York City, US: McGraw Hill, 2011. Print
[2]Image credit: https://www.doncio.navy.mil/FileHandler.ashx?id=6818
[3]Image credit: https://live.staticflickr.com/3101/3217720007_f02bc35ece.jpg


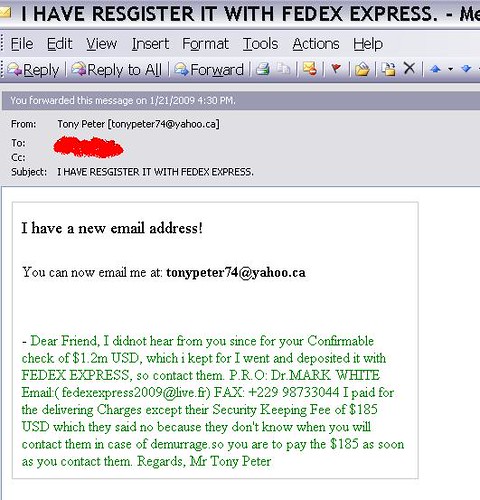
Phishing threats are growing every day. Just imagine signing up a form on an e-commerce site with your card details, and it ends up in the hands of criminals, and you just receive an alert that all your funds are gone. Geeeessssss, that’s straight depression. We just need to be more conscious.