Difference Between Encryption and Password Protection
Password protection is a process of safeguarding your online accounts from hackers or cyber criminals by using passwords in order to protect sensitive information from falling into the wrong hands. Password protection means only authorized users can access the desired information. Encryption is a level up from password protection and is more secure than passwords because sensitive information or data is encrypted or hidden using an algorithm and a key.

What is Password Protection?
Passwords are an integral aspect of the cyberspace. Password protection is a security measure put in place to protect personal and sensitive information accessible via computers from unauthorized access. Passwords protect your online accounts from hackers or cyber criminals. Passwords keep your accounts locked in the same way that door locks and burglar alarms keep the thieves or burglars out of your home. Without password protection, anyone could access your online accounts or obtain unauthorized computer or network access. Password protection means only authorized users or the ones who know the password can access the desired information. This is why a strong password is required to provide essential protection from potential identity theft and financial fraud. A password is a series of characters containing alphabets, numbers and special characters. It works like a combination of a lock on a safe and only who knows the password can access the account it is intended to protect.
What is Encryption?
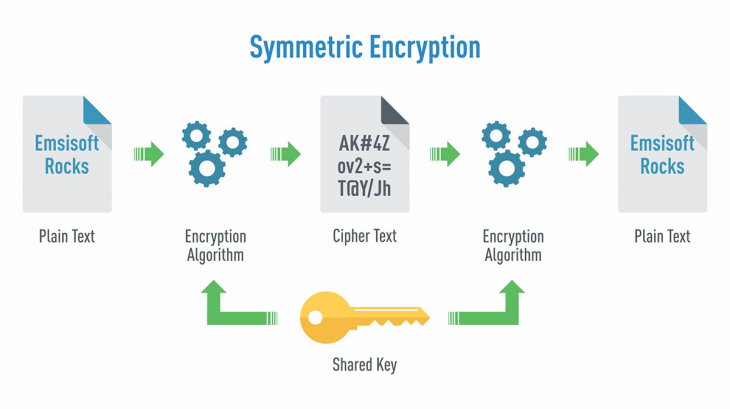
Encryption is a step up from password protection and refers to a process of concealing messages in such a way that only authorized personnel can access the information encoded within the message and unauthorized users cannot. Encryption simply means to hide information or data into something that is unreadable to anyone with no access to the information. For centuries, people have sent hidden messages that could only be read by the intended recipients to protect their secrets from falling into the wrong hands. Creating this kind of hidden message is called encryption. To hide the message, two crucial pieces of data is required: the cipher and the key. In the programming world, cipher is an algorithm and the special knowledge required to decrypt the encrypted data is called the key. So, a cipher is basically a key to the code. Today, encryption adds an extra layer of security called Secure Socket Layer (SSL) to Internet connections. So, the URL of any website using SSL starts with ‘https’ instead of ‘http’.
Difference between Encryption and Password Protection
Definition
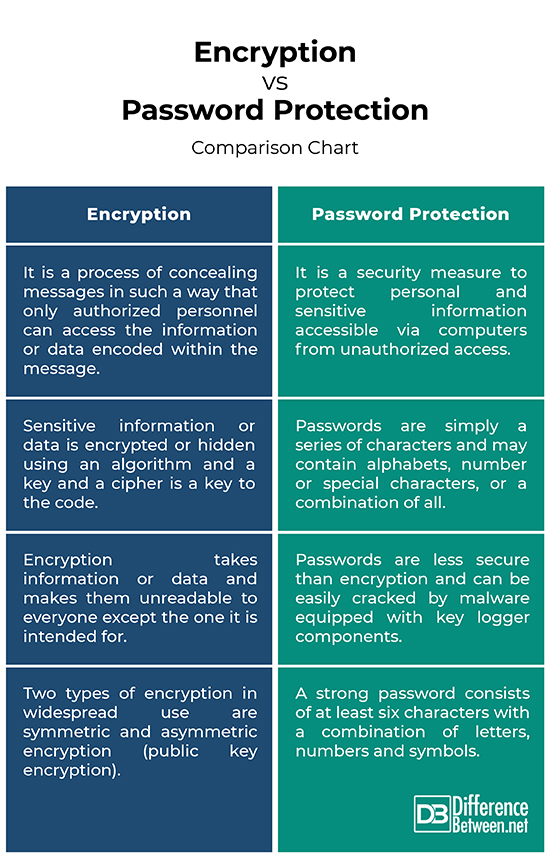
– Password is a series of characters containing ether alphabets, numbers or special characters, or a combination of all. Password protection is a security measure to protect personal and sensitive information accessible via computers from unauthorized access. Password protection means only authorized users or the ones who know the password can access the desired information. Encryption, on the other hand, is a step up from password protection and refers to a process of concealing messages in such a way that only authorized personnel can access the information or data encoded within the message.
Reliability
– A password is like a combination of a lock on a safe and only who knows the password can access the account it is intended to protect. Many applications such as email, social media applications, network connections and accounting software store passwords locally, making them vulnerable to password hacking. Also, weak passwords can be easily cracked in seconds or minutes. Encryption, on the other hand, is an added level of security which takes information or data and makes them unreadable to everyone except the one it is intended for.
Security
– Passwords are simply a series of characters and may contain alphabets, number or special characters, or a combination of all of them. Passwords are secure up to some extent, but they can be easily cracked by malware equipped with key logger components. So, using a strong password for all your online accounts is essential for your security. Encryption is more secure than passwords because sensitive information or data is encrypted or hidden using an algorithm and a key. The message can only be decrypted using the correct key and a cipher is a key to the code.
Types
– A strong password consists of at least six characters with a combination of letters, numbers and symbols. Passwords are generally case sensitive which means a strong password can have both lowercase and uppercase letters. There are two common types of encryption in widespread use: symmetric and asymmetric encryption (or public key encryption). In public key encryption, both parties have two keys – a public key that is used to encrypt a message and a private key only known to the sender and the receiver in order to decrypt the message. Symmetric encryption, on the other hand, is a type of encryption where a single key is used to both encrypt and decrypt messages.
Encryption vs. Password Protection: Comparison Chart
Summary of Encryption vs. Password Protection
Encryption is an added level of security over password protection which alters the underlying character string of a file which makes it nearly impossible to comprehend, at least not without a mechanism to decipher the file so that it can be read by the intended party. Encryption simply means to translate the data into a secret code. To read that encrypted file, you need a decryption key to decipher the code. Encrypted data is referred to as cipher text which can only be decrypted using the correct key. A cipher is a key to the code.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Image credit: https://live.staticflickr.com/1914/44405377014_2c849bb2e3_b.jpg
[1]Image credit: https://commons.wikimedia.org/wiki/File:Symmetric_encryption.png
[2]Tipton, Harold F. and Micki Krause. Information Security Management Handbook, Volume 2. Boca Raton, Florida: CRC Press, 2004. Print
[3]Beaver, Kevin. Hacking for Dummies. Hoboken, New Jersey: John Wiley & Sons, 2010. Print
[4]Cozzens, Margaret and Steven J. Miller. The Mathematics of Encryption: An Elementary Introduction. Providence, Rhode Island: American Mathematical Society, 2013. Print
[5]Ballad, Tricia and William Ballad. Securing PHP Web Applications. Noida, India: Pearson Education India, 2009. Print
