Difference Between Worm and Trojan
The digital era has given rise to a despicable set of threats – the worm and the Trojan horse. When it comes to computer security, there’s a multitude of malicious code categories available to attackers today. People often confuse these categories of malicious code. For example, people mistakenly refer to a worm as a Trojan horse. We help you clarify the differences between these two types of malicious code so you can apply the appropriate defenses.

What is a Worm?
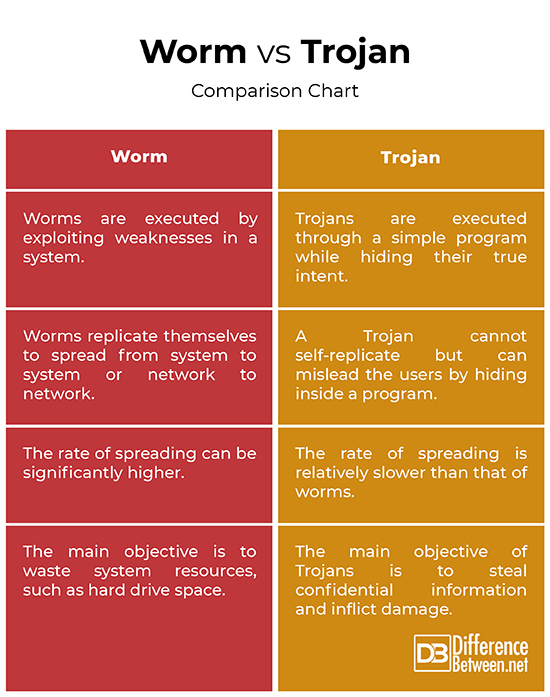
A worm is a class of software called malware that has the ability to self-replicate and spread across a network. Worms can replicate themselves and infect multiple computers on a network and can cause major damage. It can replicate without any human interaction and it does not have to piggy back onto a software program to cause damage. Worms often exploit security vulnerabilities such as security failures in a system to gain access to it.
When they infect a system, their first move is to find more systems to infect, usually by exploiting the infected system and its network connections. Worms typically use networking protocols to explore its local network and begin spreading when they find potential systems to infect. Often the systems running older operating system or using unpatched software are likely to be infected. Some worms are OS-dependent, so they only infect Windows or Linux systems.

What is a Trojan?
A Trojan horse is a type of malicious code that infects your computer system by disguising itself as a useful program while masking hidden malicious purpose. It appears as a harmless program to mislead the users of its true intent. It acts as a delivery vehicle that carries the virus to execute a variety of threats. You can recognize a Trojan horse by looking at some common signs, like poor system performance, system slowing down, spam interruptions, browser pop-ups, and so on.
According to legend, Greek warriors hid inside a wooden horse to infiltrate Troy and end a decade-long war. A Trojan horse malware works the same way. It hides inside an innocent-looking email or a downloadable software program to fool a user into thinking it’s a simple program. When you click or download, the program transfers malware to your device and finally gains access to your system.
Difference between Worm and Trojan
Type
– A worm is a class of software called malware that has the ability to self-replicate and spread across a network. A worm is like a computer program that exploits security vulnerabilities such as security failures in a system to gain access to the system. A Trojan, on the other hand, is a type of malicious code that infects your computer system by disguising itself as a useful program while hiding its true malicious intent.
Nature
– Worms replicate themselves typically using networking protocols to explore a system’s local network and begin to spread when they find potential systems to infect. They do not have to piggy back into a software program to cause damage. A Trojan, on the other hand, hides inside an innocent-looking email or program to mislead the users of its true purpose. Unlike a worm, a Trojan does not self-replicate; it is a hidden piece of code.
Objective
– The main objective of a worm is to modify or delete files or eat system resources, and mostly, to make copies of itself over and over. It copies and transfers itself from computer to computer, simply to waste system resources, such as hard drive space or bandwidth. A Trojan, on the other hand, hides its true identity to mislead the users of its main purpose, which is to steal some confidential information of users, like passwords. Trojans are meant to steal, damage, and inflict damage on your system data or network.
Worm vs. Trojan: Comparison Chart
Summary
While both worms and Trojans come under the category of malware, worms have the ability to replicating themselves, which makes the rate of spreading the virus significantly higher. Worms mainly spread to slow down the system or waste system resources. Trojans, on the other hand, do not replicate themselves like worms, but they hide inside a simple downloadable program or an email to mislead the users and eventually, steal confidential data or information of users. Trojans can give attackers backdoor access to the device, record keyword strokes, or steal sensitive user data. Trojans can also activate your camera and recording capabilities remotely to carry out malicious activities.
Which is worse virus or worm?
A worm is usually considered more dangerous than a virus because worms can spread significantly faster and infect your system more quickly. Worms can replicate and transmit themselves to other computers in a network without any human interaction.
Is worm a malware?
Yes. A worm is a type of computer malware that can replicate itself from device to device.
What is the deadliest computer virus?
ILOVEYOU, also referred to as the Love Bug, was one of the most devastating computer viruses in history that reportedly infected over 10 million personal computers.
Do Trojan horses carry viruses or worms?
A Trojan is not a virus or worm; it is a program that appears as a genuine application and tricks users into clicking them. A Trojan hides inside a program while masking its malicious purpose for carrying out attacks.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Kleymenov, Alexey and Amr Thabet. Mastering Malware Analysis. Birmingham, United Kingdom: Packt Publishing, 2019. Print
[1]Skoudis, Ed and Lenny Zeltser. Malware: Fighting Malicious Code. New Jersey, United States: Prentice Hall, 2004. Print
[2]Gregory, Peter H. Computer Viruses for Dummies. New Jersey, United States: John Wiley & Sons, 2011. Print
[3]Image credit: https://www.canva.com/photos/MABs-fnXoDY-3d-antivirus-protection/
[4]Image credit: https://www.canva.com/photos/MADAGKG5RRI-trojan/
