Difference Between Symmetric and Asymmetric Encryption
Encryption is very old. In fact, encryption has been used to send and receive confidential information in a secure way for many centuries. The Caesar’s Shift Cipher, for example, was introduced more than 2,000 years ago. Encryption simply transforms plaintext, or unprotected data, into encrypted data or cipher text, by using a key. In order to break the ciphertext and transform it back to plain text, an associated encryption key is required. It is almost impossible to break the ciphertext without the key. Early encryption methods used a single key to encrypt the plaintext to generate ciphertext and to decrypt the ciphertext into plaintext. Because the same key is used for both encryption and decryption, this method is called symmetric encryption. On the contrary, asymmetric encryption uses a pair of keys to encrypt and decrypt data; one key is used to encrypt the data and the other key is used to decrypt the data.
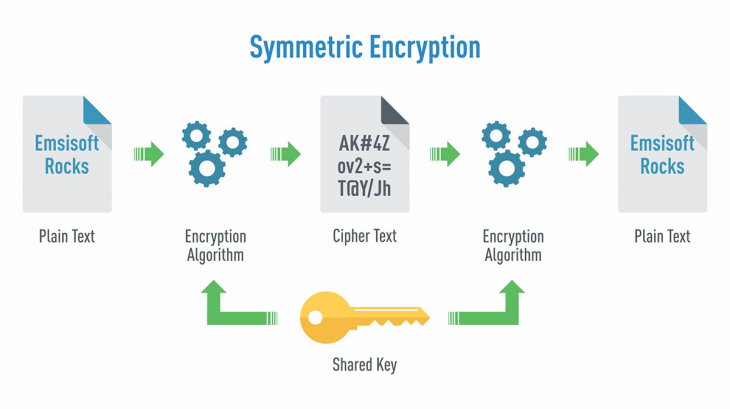
What is Symmetric Encryption?
Symmetric encryption, or single-key encryption, is a type of encryption that uses a single key to both encrypt (encode) and decrypt (decode) data or information. It is the most well understood cryptography primitive and it’s where it all started. Caesar’s cipher, the German’s Enigma, and the Japanese Purple are all examples of symmetric encryption. Every encryption algorithm requires an encryption algorithm and a decryption algorithm. In symmetric encryption, both algorithms depend on the same secret key. That single key is used to encrypt plaintext into ciphertext and to decrypt that ciphertext back into plaintext. Because the same key is responsible for encrypting and decrypting data, this method is called symmetric encryption. This type of encryption uses identical keys or keys related through a simple transformation. So, everyone with the knowledge of the secret key can decode the ciphertext into plaintext. Therefore, symmetric encryption is often called private or secret key encryption.
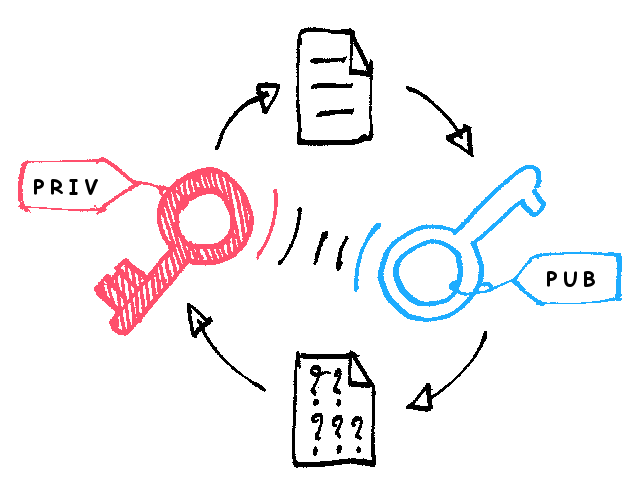
What is Asymmetric Encryption?
Asymmetric encryption, also called as public key cryptography, is a relatively new method which uses two keys, a private key and a public key, to encrypt and decrypt data. Unlike symmetric encryption, it uses a pair of keys to encrypt and decrypt data; one key is used to encrypt the data and the other key is used to decrypt the data. The public key can be distributed widely, but the private key is only known to the owner. The public key is called so because it can only be used to encrypt a message and not to decrypt it. It can be shared widely and is therefore called a public key. The sender uses its public key to encrypt the data and the receiver then uses the private key to decrypt the data. The private key is the corresponding half of the pair of keys and must always be kept secret, hence the name. It is widely used for sharing of information or data between organizations and to secure online transactions.
Difference between Symmetric and Asymmetric Encryption
Description
– Symmetric encryption, also called as single-key encryption, is a type of encryption which uses a secret key to encrypt the data and then the same key is used to decrypt the data. This means the same private key is used for both encoding and decoding information. On the contrary, asymmetric encryption, also called as public key encryption, is a type of encryption which uses a pair of keys, instead of a single key, to encrypt and decrypt data. The public key is used to encrypt data and the private key is used to decrypt the data.
Algorithms
– The widely used symmetric encryption algorithms are AES-128, AES-192, and AES-256. Other block ciphers have also been developed over the years, which include Blowfish, CAST5, IDEA, RC4, RC5, and RC6. RSA is the standard asymmetric encryption algorithm developed by Ron Rivest, Adi Shamir and Len Adleman. Well known examples of asymmetric encryption algorithms are Diffie-Hellman, ECC, ElGamal, DSA, Elliptic curve cryptography (ECC), YAK, and more.
Uses
– Symmetric encryption uses identical keys or keys related through a simple transformation. So, this type of encryption is mostly used in modern computer systems to protect user privacy and enhance security. The Advanced Encryption Standard (AES) is one of the best examples of symmetric encryption and other being Blowfish, Rivest Cipher 4, Data Encryption Standard (DES), RC5, RC6, etc. Asymmetric encryption is widely used for sharing of information or data between organizations and to secure online transactions, and digital signatures. Other applications include encrypted email, digital cash, time-stamping services, etc.
Symmetric vs. Asymmetric Encryption: Comparison Chart
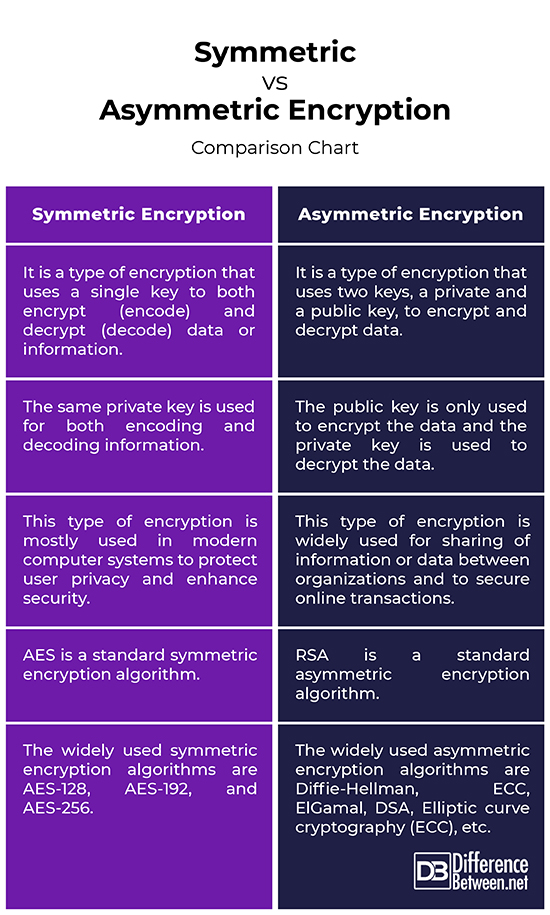
Summary of Symmetric vs. Asymmetric Encryption
In symmetric encryption, both algorithms depend on the same secret key. The same key is used to both encrypt and decrypt data. Asymmetric encryption, on the contrary, uses a pair of keys to encrypt and decrypt data; one key is used to encrypt the data and the other key is used to decrypt the data. In a nutshell, asymmetric encryption is more secure, thanks to its ability to encode information without sharing the same encryption key. However, asymmetric encryption is computationally more intensive and therefore significantly slower than symmetric encryption algorithm.
- Difference Between JPEG and RAW - April 25, 2024
- Difference Between Serif and Sans Serif - April 22, 2024
- Difference Between HTML and Text - April 19, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Image credit: https://commons.wikimedia.org/wiki/File:Asymmetric_encryption_(colored).png
[1]Image credit: https://commons.wikimedia.org/wiki/File:Symmetric_encryption.png
[2]Raymond Choo, Kim-Kwang. Secure Key Establishment. Berlin, Germany: Springer, 2008. Print
[3]Cole, Eric, et al. Network Security Fundamentals. Hoboken, New Jersey: John Wiley & Sons, 2007. Print
[4]Delfs, Hans and Helmut Knebl. Introduction to Cryptography: Principles and Applications. Berlin, Germany: Springer, 2007. Print
[5]Osuna, Alex, et al. IBM System Storage Open Systems Tape Encryption Solutions. Armonk, New York: IBM Redbooks, 2010. Print
[6]Feuerstein, Steven and Bill Pribyl. Oracle PL/SQL Programming. Sebastopol, California: O’Reilly Media, 2005. Print
