Difference Between Conventional and Public Key Encryption
One of the most significant developments in the history of cryptography came in 1976 when Whitfield Diffie and Martin Hellman published a paper called ‘New Directions in Cryptography.’ The paper introduced a groundbreaking new concept of public-key cryptography, which went on to become a fundamental element in cryptography and called Diffie-Hellman key exchange. Although, they had no practical realization of a public-key encryption at the time, the idea was clear which created an extensive interest and activity among the cryptographic community. Various standards and protocols involving cryptography have been put in place over time to deal with information security issues. The two most common encryption models are public-key encryption and conventional or single-key encryption.
What is Conventional Encryption?
Conventional encryption, also referred to as symmetric encryption or single-key encryption is a cryptographic system which uses the same key used by the sender to encrypt the message and by the receiver to decrypt the message. In this encryption model, the sender encrypts the plaintext using the receiver’s secret key, which can be later used by the receiver to decrypt the ciphertext. It is a relatively fast process since it uses a single key for both encryption and decryption. The main problem with this widely used encryption model is that this scheme does not scale well to a large number of users because both the sender and the receiver have to agree on a secret key before transmission. This makes it less secure as the key is exchanged between many senders and receivers. The idea of single-key encryption is very old, that is why it is known as conventional encryption.
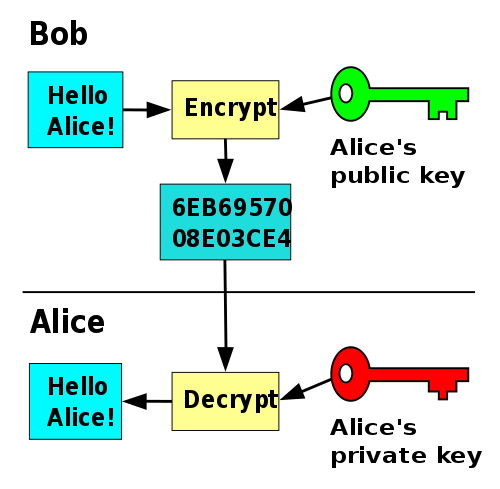
What is a Public-Key Encryption?
Public-key encryption is the first truly revolutionary concept in cryptography which was first proposed by Diffie and Hellman. Public-key encryption, also known as public-key cryptography, is a cryptographic system that uses a pair of keys: a public key and a private key. The public key can be shared freely among the users and the private key, or the secret key, is known only to the recipient. The public key is used to encrypt a message or content and the private key is then used to decrypt the message. The main objective of public-key encryption is to provide privacy, confidentiality, and authentication. Public-key algorithms are based on mathematical functions rather than on simple operations on bit patterns, such as are used in conventional encryption algorithms. In public-key encryption system, there are six main ingredients: plaintext, encryption algorithm, public key, private key, ciphertext, and decryption algorithm. It simply uses one key for encryption and a different but related key for decryption.
Difference between Conventional and Public Key Encryption
Definition
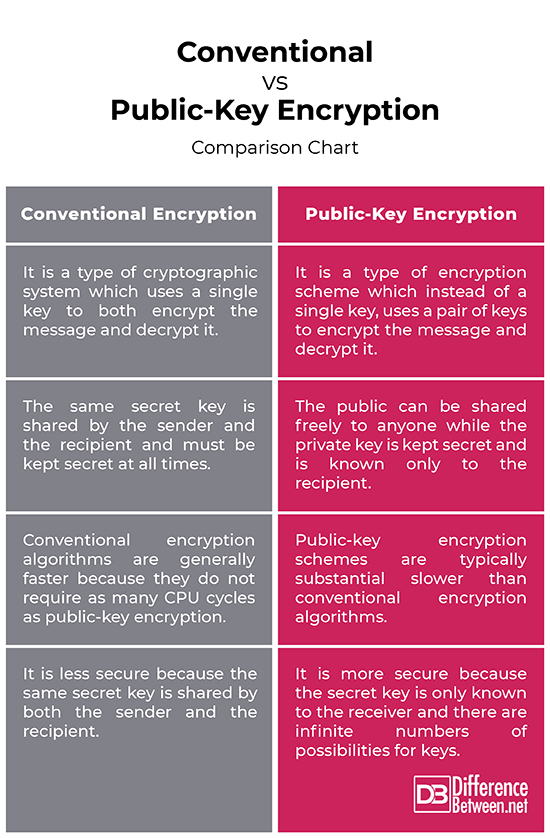
– Conventional encryption, also called as symmetric encryption or single-key encryption is a type of cryptographic system which uses a single key to both encrypt the message and decrypt it. It involves transforming plaintext into ciphertext which is to be decrypted only by the intended receiver. Public-key encryption, also known as asymmetric encryption, is a type of encryption scheme which instead of a single key, uses a pair of keys – a public key and a private key. The public key is used to encrypt a message and the private key is then used to decrypt the message.
Key
– The key used in the conventional encryption scheme is typically referred to as a secret key which is shared by both sender and receiver and must be kept secret by the systems involved in the encryption and decryption processes. If this secret key is disclosed, the communications will be compromised. The two keys used for public-key encryption are referred to as the public key and the private key. The public key is used to encrypt the messages and can be shared freely among the users, but the private key is kept secret and is only known to the recipient, used to decrypt the messages.
Security
– With the conventional encryption model, both the sender and the receiver must know the secret key ahead of time and they have to agree on the key before transmission, which raises security concerns and a problem of trust, especially when it comes to authentication and integrity checking. It’s hard to keep the key secret when the encryption and decryption happens in different locations. Public-key encryption, on the other hand, is more secure because the pair of keys is based on prime numbers of long length meaning there is infinite number of possibilities for keys.
Conventional vs. Public-Key Encryption: Comparison Chart
Summary
The main objective of encryption is to ensure privacy, confidentiality, and authentication. However, a primary advantage of public-key encryption system is that providing authentic public keys is relatively easier than distributing secret keys, as required in conventional encryption systems. Public-key encryption systems, however, are substantially slower than their conventional counterparts. For this reason, these systems are mostly used for bulk data encryption by symmetric algorithms, and for encrypting small data items such as credit card number and PINs.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Menezes, Alfred J., et al. Handbook of Applied Cryptography. Boca Raton, Florida: CRC Press, 1996. Print
[1]Menezes, Alfred J., et al. Handbook of Applied Cryptography. Boca Raton, Florida: CRC Press, 1996. Print
[2]Umar, Amjad. Information Security and Auditing in the Digital Age: A Practical Managerial Perspective. Plantation, Florida: NGE Solutions, 2003. Print
[3]Stallings, William. Network Security Essentials: Applications and Standards. New Delhi, India: Pearson Education India, 2007. Print
[4]Srinathan, K., et al. Progress in Cryptology – INDOCRYPT 2007: 8th International Conference on Cryptology in India, Chennai, India, December 9-13, 2007, Proceedings. Berlin, Germany: Springer, 2007. Print
[5]Image credit: https://upload.wikimedia.org/wikipedia/commons/9/9f/Enigma_rotor_set.png
[6]Image credit: https://upload.wikimedia.org/wikipedia/commons/thumb/f/f9/Public_key_encryption.svg/500px-Public_key_encryption.svg.png
