Difference Between DMZ and Firewall
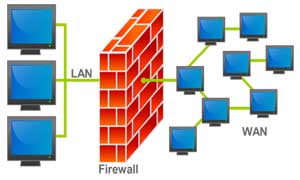
The first of these is the firewall which is placed between your network and the internet. It is used to block unauthorized communication from the internet going into your network while allowing authorized communications to go through. You can imagine the firewall as a security guard screening people. Although there are some disadvantages to a firewall, like small penalties in performance, it is always necessary to have one.
The second strategy often employed by companies is the DMZ or Demilitarized Zone, which sounds like it should belong in North Korea. A DMZ is simply a method of networking arrangement, by segregating servers that are often accessed from the outside. Services like mail servers and http servers are accessed from the outside very often, this might cause a bit of a security risk when these servers are in the same network as your servers that contain confidential data. To understand it better, you can compare this method to a casino. Once you enter a casino you would get screened by a guard, but you can’t go everywhere in a casino except the floor. Certain areas like the vault and the control centers are off limit unless you are an authorized personnel, and the doors to these areas are often guarded with much stricter rules than at the door. In the same manner, the firewall allows most traffic to access services in the DMZ while applying stricter rules when trying to access internal servers.
Security systems might be difficult to implement at times, but these are necessary to provide uninterrupted service while protecting the data that is meant for internal use only. The firewall and the DMZ are the two most commonly used methods of protecting your own servers, but do not limit yourself to these two. You should always be on the lookout for new threats and ways that you can protect yourself from these threats.
- Difference Between Sony Cybershot S Series and W Series - December 22, 2012
- Difference Between Samsung Galaxy S3 and iPhone 5 - December 21, 2012
- Difference Between Samsung Galaxy S2 (Galaxy S II) and Galaxy S 4G - December 20, 2012
