Difference Between SHA-256 and SHA-1
SHA, short for Secure Hash Algorithm, is a family of cryptographic hashing algorithm published by the National Institute of Standards and Technology (NIST) to keep your data secured. In 1995, the NIST approved the Secure Hash Standard, FIPS PUB 180-1, which included one secure hash algorithm, the SHA-1. In 2003, a new Secure Hash Signature Standard (SHS), FIPS PUB 180-2 was approved, adding three hash algorithms capable of producing larger message digests, outperforming the FIPS 180-1. The FIPS PUB 180-2 specifies four secure hash algorithms, SHA-1, SHA-256, SHA-384, and SHA-512 – all of which are iterative, i.e., one-way hash functions that can process a message in a condensed representation called a message digest. Mainly because of their efficiency, cryptographic hash functions are of central importance for cryptographic algorithms and protocols.
This article will mainly focus on the two popular cryptographic hash functions is use today – SHA-1 and SHA-256. Part of the Secure Hash Standard (SHS), SHA-1 was one of the earliest hash algorithms often used by SSL certificate authorities to sign certificates. It was published in 1993 as SHA but because of a security flaw, it was later replaced by the more secure SHA-1. It is by far one of the most widely used and deployed cryptographic hash functions. SHA-256 has the same underlying structure and uses the same type of modular arithmetic and logical binary operations as SHA-1. SHA-256 belongs to the SHA-2 family of similar hash functions with different block size, the other being SHA-512. It is a hash function commonly used in Blockchain.
What is SHA-1?
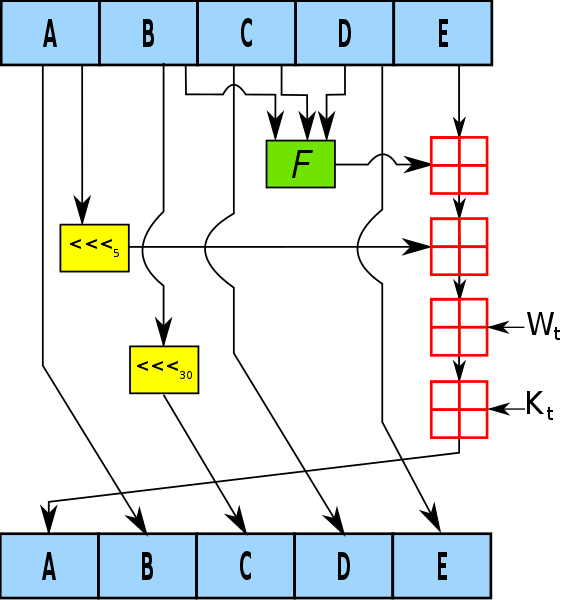
SHA-1 is one of the most widely used and deployed cryptographic hash functions often used by SSL certificate authorities to sign certificates. It was one of the oldest hash algorithms specified for use by the U.S. federal government. It was developed by NIST and the NSA. SHA-1 was published as a federal government standard in 1995 as an update to the SHA, which was published in 1993. It takes an input and produces a 160-bit (20-byte) hash value known as a message digest, typically represented by a 40-digit long hexadecimal string. The SHA-1 is designed so it is computationally infeasible to find a message that corresponds to a given message digest, or to find two different messages which produce the same message digest.
What is SHA-256?
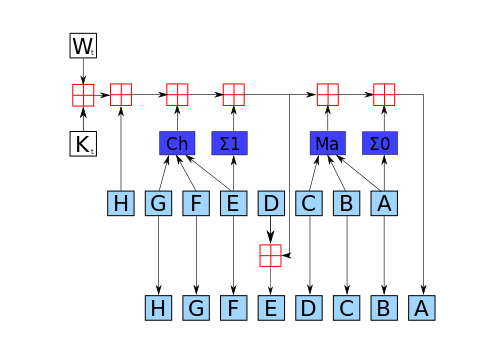
SHA-256 is a newer, more secure cryptographic hash function which was proposed in 2000 as a new generation of SHA functions and was adopted as FIPS standard in 2002. The SHA-256 algorithm generates a 256-bit hash value from padded 512-bit message blocks, and the original message size is up to 264-1 bits. SHA-256 always computes a 256-bit hash internally for security, but this resulting can be truncated to either 196 or 128 bits printing and storage. Thus a truncated SHA-256 yields a substantial benefit for human usability in printed citations, and significantly improves security, at the cost of a small reduction in performance related to MD5. Unlike the MD5 algorithm, truncated SHA-256 is not subject to any known attacks.
Difference between SHA-256 and SHA-1
Basic of SHA-256 and SHA-1
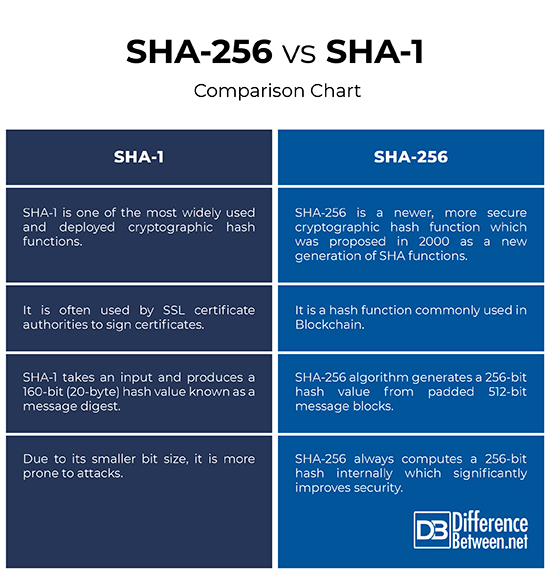
– SHA-1 is one of the most widely used and deployed cryptographic hash functions often used by SSL certificate authorities to sign certificates. It was one of the oldest hash algorithms specified for use by the U.S. federal government. SHA-256 is a newer, more secure cryptographic hash function which was proposed in 2000 as a new generation of SHA functions and was adopted as FIPS standard in 2002. SHA-256 belongs to the SHA-2 family of cryptographic hashing algorithms with similar hash functions but different block size, others being SHA-384 and SHA-512.
Block Size
– SHA-1 is a 160-bit hash takes an input and produces a 160-bit (20-byte) hash value known as a message digest, typically represented by a 40-digit long hexadecimal string. The SHA-1 is designed so it is computationally infeasible to find a message that corresponds to a given message digest, or to find two different messages which produce the same message digest. The SHA-256 algorithm generates a 256-bit hash value from padded 512-bit message blocks, and the original message size is up to 264-1 bits.
Performance
– With the increasing computing power, the feasibility of breaking the SHA-1 has also increased. It was one of the oldest hash algorithms specified for use by the U.S. federal government and due to its smaller bit size, it is more prone to attacks. Although SHA-256 has the same underlying structure and uses the same types of modular arithmetic and logical binary operations as SHA-1, it has become an integral part in many applications. SHA-256 always computes a 256-bit hash internally for security, which significantly improves security, at the cost of a small reduction in performance related to MD5.
SHA-256 vs. SHA-1: Comparison Chart
Summary of SHA-256 verses SHA-1
In a nutshell, SHA-256 is more reliable and secure than SHA-1. SHA-256 belongs to the family of SHA-2 cryptographic hash functions designed by the NSA and is commonly used in Blockchain. SHA-1 was one of the earliest cryptographic hash functions often used by SSL certificate authorities to sign certificates. However, due to its smaller bit size and security vulnerabilities, it has become more prone to attacks over time which eventually led to its depreciation from SSL certificate issuers.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Image credit: https://upload.wikimedia.org/wikipedia/commons/thumb/0/09/SHA256.svg/500px-SHA256.svg.png
[1]Image credit: https://upload.wikimedia.org/wikipedia/commons/thumb/e/e2/SHA-1.svg/500px-SHA-1.svg.png
[2]Stallings, William. Cryptography And Network Security (4th ed.). London: Pearson Education, 2006. Print
[3]Mogollon, Manuel. Cryptography and Security Services. Pennsylvania: IGI Global, 2008. Print
[4]Oppliger, Rolf. Security Technologies for the World Wide Web. Norwood, Massachusetts: Artech House, 2003. Print