Difference Between Data Breach and Security Breach
Every now and then, we hear in the news and read articles about systems being compromised in one or multiple organizations and the data of millions of people being exposed. In fact, data breaches have become so frequent that we woke up to hearing about one almost every day. Well, there has been a steady rise in the number of data breaches in the United States since 2011; 614 data breaches have been reported in 2013 alone, followed by over 1,000 reports in 2016, and the number keeps increasing. We tend to think of a security breach as a result of a cyber crime, but it’s more than what meets the eye. So, what exactly are data breaches? And are they similar in nature to security breaches? Let’s find out.

What is Data Breach?
When you Google search the term “data breach”, you’ll come across over a million of search results, many with conflicting definitions of what exactly a data breach is. A data breach, in general, is a confirmed security incident which involves intentional or unintentional access, disclosure, or destruction of private or confidential information by a malicious third party. Organizations experience a significant number of events almost every single day, a subset of those events classify as security incidents and a subset of those security incidents can be classified as breaches.
Information privacy plays an important role in today’s modern-age society. But, it also becomes an issue of growing public concern. Big companies and organizations, and even governments collect and generate tons of sensitive information every day, which is often a byproduct of their day-to-day operations. Data breaches involve exposure of such information which often includes private data such as social security numbers, credit card numbers, healthcare history, as well as corporate data. So, if anyone who is not authorized to view or access such data gets their hands on the data, the organization or the company said to have a data breach.

What is Security Breach?
A security incident (or security breach) is an event related to a system, network or individual that involves altering the target’s state by any means possible, whether it’s a violation of an organization’s security, privacy and regulatory policies or exposure of their confidential data. A security breach refers to any unauthorized access to a system, network or devices, which might result in the system being compromised or information being exposed without authorization. Typically, a security breach is any security incident that involves a malicious third party or a professional hacker being able to access a system or a security mechanism they are not authorized to access.
Technically, a security breach is not the same as a data breach. All data breaches are essentially security breaches, but not all security breaches can be classified as data breaches. A data breach refers to unauthorized access to confidential data, while a security breach is an all-encompassing term that involves all kinds of security incidents, including data breaches. But, security breaches can cost organizations a huge deal of money and credibility. Organizations face such incidents on any given day and it’s actually shocking that the number of security incidents that actually get reported is just a small fraction of what actually occurs.
Difference between Data Breach and Security Breach
Definition
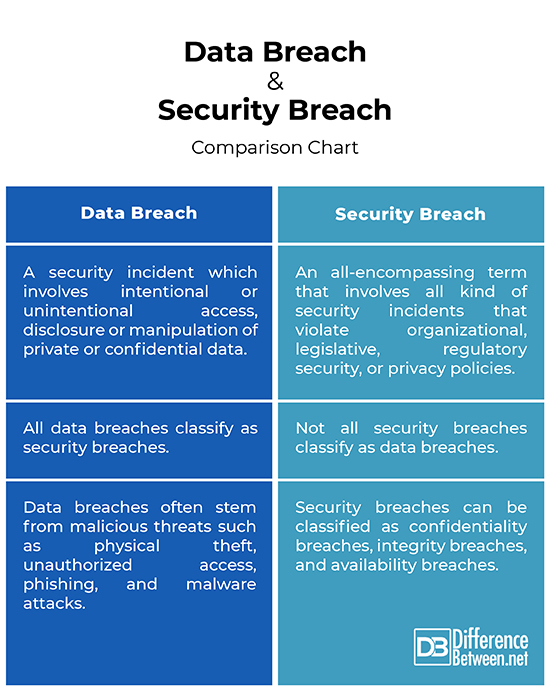
– A data breach is a type of security incident which involves intentional or unintentional access, disclosure or manipulation of private or confidential data by a suspicious third party without the knowledge of the owner of the data. It basically exposes sensitive or protected information to an unauthorized party. A security breach is an all-encompassing term that involves all kind of security incidents that violate an organizational, legislative, regulatory security, or privacy policies. Basically, all data breaches are security breaches, but not all security breaches can be classified as data breaches.
Source
– Data breaches are a result of several incidents, the most common being: a targeted cyber attack by a single or a group of criminals who is/are targeting a specific organization; an attack perpetrated by a criminal looking for vulnerabilities in a system; or inadvertently through manual errors such as by an employee who accidentally loses some confidential data. Security breaches, in general, can be classified as confidentiality breaches, integrity breaches, and availability breaches. Data breaches often stem from malicious threats such as hacking intrusions, physical theft, unauthorized access, phishing, and malware attacks.
Impact
– While a security breach is not the same as a data breach, the consequences of a security breach can be a lot to take in. Significant revenue loss is one of the most common aftereffects of a security breach, along with loss of customer trust, operational downtime, damage to reputation, loss of sensitive data, security costs, direct fines and fees, and more. The immediate effects of a security breach are less well known, but can be very damaging. So, the question is how quickly an organization can identify and contain the breach.
Data Breach vs. Security Breach: Comparison Chart
Summary
While a data breach can be classified as a security breach, they are not same and the two cannot be used interchangeably. Data breaches are a type of security incidents that involve access, disclosure and manipulation of confidential data without the knowledge of the owner of the data. A security breach, on the other hand, that involves all kind of security incidents that violate organizational, legislative, regulatory security, or privacy policies. So, in a nutshell, all data breaches are security breaches, but not all security breaches can be classified as data breaches.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Fowler, Kevvie. Data Breach Preparation and Response: Breaches are Certain, Impact is Not. Massachusetts, United States: Syngress, 2016. Print
[1]Solove, Daniel J. and Paul M. Schwartz. Consumer Privacy and Data Protection. New York, United States: Wolters Kluwer, 2020. Print
[2]Mitchell, Stewart. How to Survive a Data Breach: A Pocket Guide. Cambridgeshire, United Kingdom: IT Governance Publishing, 2009. Print
[3]Davidoff, Sherri. Data Breaches: Crisis and Opportunity. Massachusetts, United States: Addison-Wesley Professional, 2019. Print
[4]Image credit: https://live.staticflickr.com/65535/48409895557_fbb3f5542c_b.jpg
[5]Image credit: https://live.staticflickr.com/8116/29723649810_8cb4a06489_b.jpg
