Difference Between Static Malware Analysis and Dynamic Malware Analysis
Malware analysis is a process or technique of determining the origin and potential impact of a specified malware sample. Malware could be anything that looks malicious or acts like one like a virus, worm, bug, Trojan, spyware, adware, etc. Any suspicious software that may cause harm to your system can be considered as a malware. Regardless of the increasing use of anti-malware software programs, the world is witnessing a rapid evolution in malware attacks. Anything that is connected to the Internet is prone to malware attack.
Malware detection continues to pose challenge as potential attackers find new and advanced ways to escape from detection methods. This is where malware analysis comes to the picture.
Malware analysis gives a better understanding of how a malware functions and what can be done to eliminate those threats. The malware analysis can be done with different objectives in mind like to understand the extent of malware infection, to know the repercussions of the malware attack, to identify the nature of the malware, and to determine the functionalities of the malware.
There are two types of methods used for malware detection and analysis: Static Malware Analysis and Dynamic Malware Analysis. Static analysis involves examining the given malware sample without actually running it, whereas Dynamic analysis is carried out systematically in a controlled environment. We present an unbiased comparison between the two to help you better understand the methods of malware analysis.
What is Static Malware Analysis?
Static analysis is a process of analyzing a malware binary without actually running the code. Static analysis is generally performed by determining the signature of the binary file which is a unique identification for the binary file and can be done by calculating the cryptographic hash of the file and understanding each component.
The malware binary file can be reverse-engineered by loading the executable into a disassembler such as IDA. The machine-executable code can be converted assembly language code so that it can be easily read and understood by humans. The analyst then looks at the program to have a better understanding of what it is capable of and what it’s programmed to do.

What is Dynamic Malware Analysis?
Dynamic analysis involves running the malware sample and observing its behavior on the system in order to remove the infection or stop it from spreading into other systems. The system is setup in a closed, isolated virtual environment so that the malware sample can be studied thoroughly without the risk of damage to your system.
In advanced dynamic analysis, a debugger can be used to determine the functionality of the malware executable which otherwise would have been difficult to obtain using other techniques. Unlike static analysis, it’s behavior-based so it’s hard to miss important behaviors.
Difference between Static and Dynamic Malware Analysis
Meaning of Static and Dynamic Malware Analysis
Malware can behave differently depending on what they are programmed to do which makes it all the more important to understand their functionalities. There are basically two methods to do so: Static Analysis and Dynamic Analysis. Static analysis is a process of determining the origin of malicious files to understand their behavior without actually executing the malware. Dynamic analysis, on the other hand, is a more detailed process of malware detection and analysis carried out in a controlled environment and the whole process is monitored to observe the behavior of the malware.
Analysis
Static malware analysis is a quite simple and straightforward way to analyze a malware sample without actually executing it so the process does not require the analyst to go through each and every phase. It simply observes the behavior of the malware to determine what it is capable of or what it can do to the system. Dynamic malware analysis, on the other hand, involves a thorough analysis using the behavior and actions of the malware sample while in execution to have a better understanding of the sample. The system is setup in a closed and isolated environment with proper monitoring.
Technique involved in Static and Dynamic Malware Analysis
Static analysis involves analyzing the signature of the malware binary file which is a unique identification for the binary file. The binary file can be reverse-engineered using a disassembler such as IDA to convert the machine-executable code into assembly language code to make it human readable. Some of the techniques used for static analysis are file fingerprinting, virus scanning, memory dumping, packer detection, and debugging. Dynamic analysis involves analyzing the behavior of malware in a sandbox environment so that it won’t affect other systems. Manual analysis is replaced by automated analysis through commercial sandboxes.
Approach
Static analysis uses a signature-based approach to malware detection and analysis. A signature is nothing but a unique identifier for a specific malware which is a sequence of bytes. Different patterns are used to scan for signatures. Signature-based antimalware programs are effective against most common types of malware, but are ineffective against sophisticated and advanced malware programs. This is where dynamic analysis comes to picture. Instead of a signature-based approach, dynamic analysis uses a behavior-based approach to determine the functionality of the malware by studying the actions performed by the given malware.
Static vs. Dynamic Malware Analysis: Comparison Chart
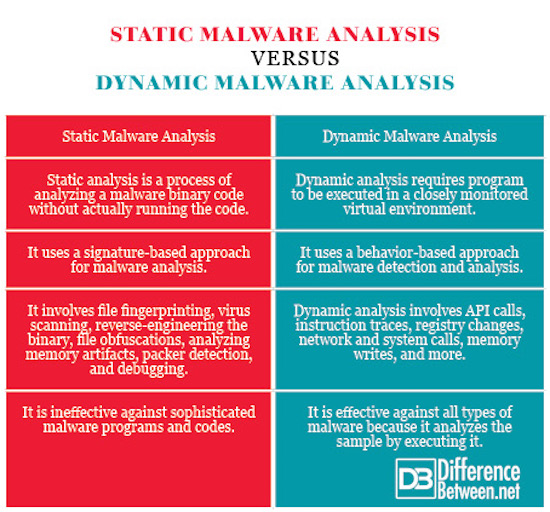
Summary of Static Vs. Dynamic Malware Analysis
Detection, identification, and preliminary analysis is crucial to malware analysis and it is very much necessary to run a system analysis to contain the spread of malware so that to stop it from spreading into other productive systems or files and directories. In this article, we compared malware detection techniques based on static and dynamic malware analysis. Both are the widely used techniques for malware detection, except static analysis uses a signature-based approach whereas dynamic analysis uses a behavior-based approach to malware detection. Regardless of the technique used for malware detection, both the methods allows us to have a better understanding of how the malware functions and what can we do about it.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Image credit: https://pixabay.com/en/ransomware-virus-malware-hacker-2321665/
[1]Image credit: https://www.flickr.com/photos/32936091@N05/3752997536
[2]Sikorski, Michael and Andrew Honig. Practical Malware Analysis. San Francisco: No Starch Press, 2012. Print
[3]Elisan, Christopher C. Advanced Malware Analysis. NYC: McGraw Hill Professional, 2015. Print
[4]Case, Andrew, et al. The Art of Memory Forensics: Detecting Malware and Threats in Windows, Linux, and Mac Memory. New Jersey: John Wiley & Sons, 2014. Print
