Difference Between MDM and MAM
Companies have started encouraging and adopting the “bring your own device” (BYOD) initiative for quite some time. However, BYOD has moved beyond the use of laptops over the years. Although, mobile technologies can be accommodated through standard corporate-issued devices or through the concept of BYOD, mobile technology raises new problems, particularly in terms of security. Previously, it was easy to deal with mobility. However, the new mobile devices are not so easy to manage and on top of it, enterprises have to deal with the security of personal devices in the workplace. To tackle these issues, the enterprise mobility management (EMM) industry has come up with a solution – to implement technologies like mobile device management (MDM) and mobile application management (MAM). So, what is MDM and what is MAM, and what are the differences between the two? Let’s take a look.

What is MDM?
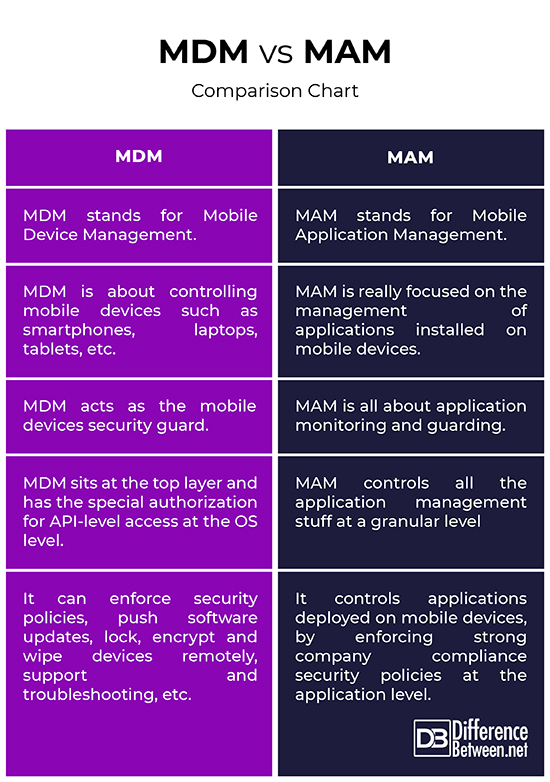
MDM, short for Mobile Device Management, is a technology-backed tool used by administrators to monitor, manage and secure employees’ mobile devices, including laptops or tablets, in addition to managing mobile applications that are being used in the organization. MDM is enterprise security software that controls and secures smartphones, tablets, or laptops used by the employees for company purposes. It allows IT administrators to push software updates, remotely wipe clean the devices, manage user settings, or administer organization compliance policies on mobile work devices. MDM solutions are the top priority on most of the corporate houses. This applies for both employee-owned and company-issued mobile devices. MDM is a broad category of product offerings from multiple vendors allowing corporate companies to manage its complete mobile device deployment lifecycle – from initial configuration to management, troubleshooting and support, everything.

What is MAM?
MAM, short for Mobile Application Management, is part of MDM’s broad category of product offerings that enables IT administrators to secure, control, manage, and deploy enterprise applications on both personal and corporate-issued mobile devices. It is similar to MDM but for applications instead of devices. Similarly, MAM refers to a range of software and services that allows companies to create a private application catalog that works just like a public marketplace. This is similar to validating specific applications as safe applications, based on the criteria of your choice. It authorizes IT administrators to control applications deployed on mobile devices, by enforcing strong company compliance security policies. The policies may include monitoring all the applications installed on your mobile devices in your network, along with viewing details of each application such as determining which services are accessing which applications, and so on. They are authorized to prompt users to uninstall those applications that are a security risk to the organization or are not corporate-approved.
Difference between MDM and MAM
Meaning
– MDM is a set of corporate compliance software solutions used by IT administrators to monitor, manage and secure employees’ mobile devices, including laptops or tablets, in addition to managing mobile applications that are being used in the organization. MAM, on the other hand, is part of MDM’s broad category of product offerings that enables IT administrators to securely manage and control applications deployed on mobile devices without having to manage the devices. MAM is similar to MDM but for applications instead of devices.
Approach
– MDM is about controlling mobile devices such as smartphones, laptops, tablets, etc. IT administrators are authorized to use MDM to enforce security policies, push software updates, lock, encrypt and wipe devices remotely, support and troubleshooting, so, basically they control the devices. MAM, on the other hand, is really focused on the management of applications, authorizing IT administrators to monitor applications installed on your devices, data wipe around an application, or prompt users to uninstall applications that are not corporate-approved.
Features
– Both MDM and MAM offer enterprise security solutions, but in a different context. However, they do share some grounds such as data loss prevention, blacklisting and whitelisting of devices, applications, etc., management of B2C applications, remote data wipe, and so on. However, there are some features that one has and the other doesn’t. For example, MDM offers encryption of device data whereas MAM offers two-factor authentication on applications; MDM authorizes installation or uninstallation of applications remotely whereas MAM allows remote data injection both on user and application level, and there’s more.
MDM vs. MAM: Comparison Chart
Summary
Mobile device management (MDM) has a direct impact on the security of both your personal and company-issued mobile devices deployment lifecycle. One of the most fundamental elements of MDM is to manage devices remotely wherein the IT administrator is authorized to wipe clean the devices remotely or enforce security policies at the device level. MAM, on the other hand, is all about application management and focused on certain corporate applications and their associated data. MAM allows you to safeguard your company’s data within an application whereas MDM sits at the highest level keeping your corporate data and information safe. If a mobile device is lost or stolen, MDM I authorized to wipe clean all data of the device remotely.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
 Email This Post
: If you like this article or our site. Please spread the word. Share it with your friends/family.
Email This Post
: If you like this article or our site. Please spread the word. Share it with your friends/family.
Leave a Response
References :
[0]Udell, Chad. Mastering Mobile Learning. New Jersey, United States: John Wiley & Sons, 2014. Print
[1]Collins, Lauren and Scott R. Ellis. Mobile Devices: Tools and Technologies. Florida, United States: CRC Press, 2015. Print
[2]Campagna, Rich et al. Mobile Device Security For Dummies. New Jersey, United States: John Wiley & Sons, 2011. Print
[3]Pierer, Markus. Mobile Device Management: Mobility Evaluation in Small and Medium-Sized Enterprises. Berlin, Germany: Springer, 2016. Print
[4]Image credit: https://media.defense.gov/2019/Jul/16/2002158147/-1/-1/0/190716-F-RU983-999.JPG
[5]Image credit: https://www.public.navy.mil/surfor/PublishingImages/150211-N-HM833-001.jpg

