Difference Between Penetration Test and Vulnerability Scan
The following two tests – penetration testing (or pen testing) and vulnerability assessment – have gained widespread importance in the last couple of years. Organizations have a complex network of assets that store sensitive data. Such assets are prone to potential threats from both within and outside the organization. To identify and eliminate such threats, conducting a security assessment of the whole security infrastructure is essential. But understanding the difference between the two is equally important.

What is Penetration Testing?
Penetration testing, or pen testing, is a threat assessment strategy that involves simulating real attacks to evaluate the risks associated with potential security breaches. It is a simulated cyberattack against your computer system to uncover potential vulnerabilities that could hamper the security of your system. In an organizational setting, pen testing serves as a security measure to assess the organization’s security protocols and policies and to make sure they are effective against any sort of attacks.
Sometimes called ethical hacking, pen testing is intended to seek out exploitable vulnerabilities against an organization’s security infrastructure. It has become an integral part of a comprehensive security program. It exploits weaknesses on systems or entire IT infrastructure to uncover any threats that could harm your operating systems, network devices, and application software. The idea is to find and secure those weaknesses before the attack.

What is Vulnerability Scan?
Vulnerability assessment, or vulnerability scan, is a systematic approach to identifying risks and vulnerabilities in computer systems, network devices, hardware, and applications. It is the process of reviewing, classifying, and prioritizing vulnerabilities in a system before hackers exploit them. Businesses today are highly dependent on information technology including the cloud, which also increases the risk of getting exploited by potential hackers.
A vulnerability management program like vulnerability assessment can help to identify weaknesses before they become problems. The majority of cyber attacks exploit known vulnerabilities with new vulnerabilities being identified every year. So, the idea is to identify and classify as many defects as possible based on their security levels in a given timeframe. Vulnerability assessment is a comprehensive threat assessment program that identifies and quantifies the security weaknesses in a system.
Difference between Penetration Test and Vulnerability Scan
Strategy
– While both pen testing and vulnerability assessment come under the threat assessment category; there are subtle differences between the two. Vulnerability assessment checks for known weaknesses in a system and generates a report on risk exposure, whereas pen testing is meant to exploit weaknesses on a system or an entire IT infrastructure to uncover any threats to the system.
Scope
– The scope of pen testing is targeted and there is also a human factor involved. Pen testing not only involves discovering vulnerabilities that could be used by attackers but also exploiting those vulnerabilities to assess what attackers can exploit after a breach. So, vulnerability assessment is one of the essential prerequisites for doing a pen test. Unless you’re familiar with the weaknesses in a target system, you are not able to exploit them.
Approach
– A vulnerability assessment, as the name suggests, is a process that scans computer systems and network devices for security weaknesses. It is an automated process performed with the help of automated tools to scan for new and existing threats that can harm your system. Pen testing, on the other hand, requires a well-planned, methodological approach and is performed by experienced individuals who understand all the facets of security posture.
Penetration Test vs. Vulnerability Scan: Comparison Chart
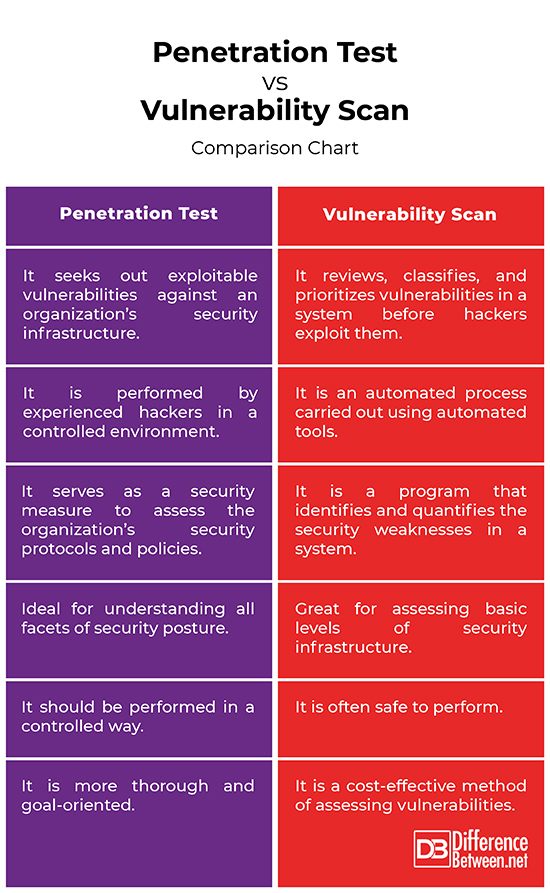
Summary of Penetration Test verses Vulnerability Scan
Vulnerability assessment is a cost-effective service that serves its purpose of identifying low-hanging weaknesses in a system posture. It is a low-risk threat assessment approach to identifying known weaknesses in a system and generating a report on risk exposure. Penetration testing, on the other hand, is a methodological approach that involves rigorous assessment to exploit weaknesses on a system or an entire IT infrastructure. Pen testing is a controlled form of hacking that simulates real attacks to evaluate the risks associated with potential security breaches.
Which is better vulnerability assessment or penetration testing?
Pen testing involves more rigorous assessment and scanning of systems – it is a controlled form of hacking performed in a controlled environment to avoid causing damage to the target system. Vulnerability scans are often safe to perform and are executed using automated tools. Pen testing, however, has its own set of risks.
Why is a penetration test considered to be more thorough than a vulnerability scan?
Pen testing is one of the most effective ways to identify weaknesses in a system. It is meant to assess the feasibility of systems against potential threats or breaches. It is carried out in a more controlled environment by experienced hackers.
Does penetration test necessary why or why not?
A penetration test seeks to identify potential vulnerabilities in a system before an attacker does, and recommends how to fix those issues and avoid future vulnerabilities. The scope of a pen test varies from system to system or client to client. It verifies the ability of a system to protect itself from malicious attacks.
Is penetration testing effective?
Penetration testing is very effective as it simulates real attacks to evaluate the risks associated with potential security breaches. It is intended to identify weaknesses in security infrastructure.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Weidman, George. Penetration Testing: A Hands-On Introduction to Hacking. California, United States: No Starch Press, 2014. Print
[1]Rahalkar, Sagar. Quick Start Guide to Penetration Testing: With NMAP, OpenVAS and Metasploit. New York, United States: Apress, 2018. Print
[2]Rahalkar, Sagar. Network Vulnerability Assessment: Identify Security Loopholes in Your Network’s Infrastructure. Birmingham, United Kingdom: Packt Publishing, 2018. Print
[3]Image credit: https://www.canva.com/photos/MAEEUje_kRw-email-vulnerability-scan/
[4]Image credit: https://www.canva.com/photos/MADnNag7GQk-fingerprint-biometric-digital-scan-technology-/
